Data model
Introduction
The OpenCTI core design relies on the concept of a knowledge graph, where you have two different kinds of object:
- Nodes are used to describe
entities, which have somepropertiesorattributes. - Edges are used to describe
relationships, which are created between twoentitynodes and have somepropertiesorattributes.
Example
An example would be that the entity APT28 has a relationship uses to the malware entity Drovorub.
Standard
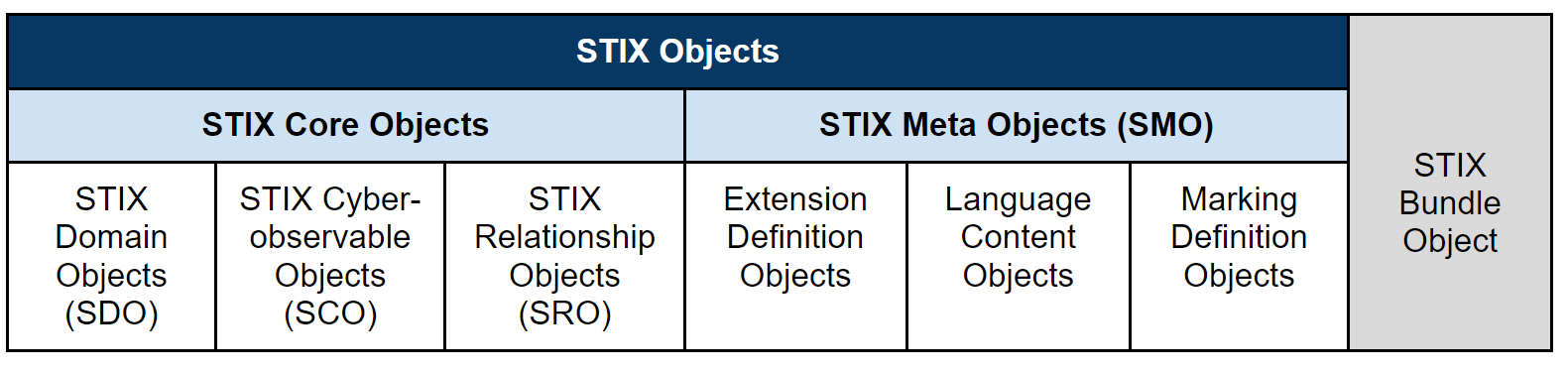
The STIX model
To enable a unified approach in the description of threat intelligence knowledge as well as importing and exporting data, the OpenCTI data model is based on the STIX 2.1 standard. Thus we highly recommend to take a look to the STIX Introductory Walkthrough and to the different kinds of STIX relationships to get a better understanding of how OpenCTI works.
Some more important STIX naming shortcuts are:
- STIX Domain Objects (SDO): Attack Patterns, Malware, Threat Actors, etc.
- STIX Cyber Observable (SCO): IP Addresses, domain names, hashes, etc.
- STIX Relationship Object (SRO): Relationships, Sightings
Extensions
In some cases, the model has been extended to be able to:
- Support more types of SCOs to modelize information systems such as cryptocurrency wallets, user agents, etc.
- Support more types of SDOs to modelize disinformation and cybercrime such as channels, events, narrative, etc.
- Support more types of SROs to extend the new SDOs such as
amplifies,publishes, etc.
Implementation in the platform
Diagram of types
You can find below the digram of all types of entities and relationships available in OpenCTI.
Attributes and properties
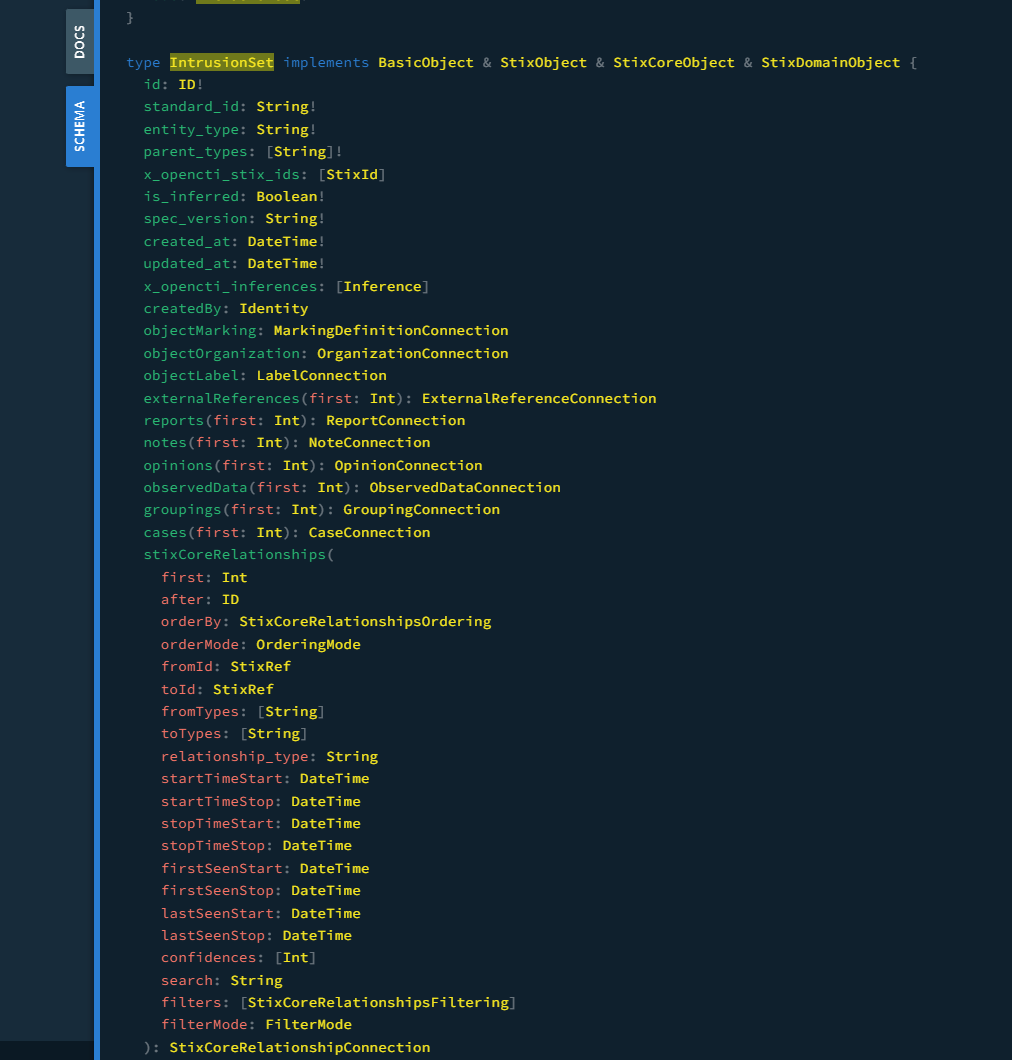
To get a comprehensive list of available properties for a given type of entity or relationship, you can use the GraphQL playground schema available in your "Profile > Playground". Then you can click on the Documentation button on the left. You can for instance search for the keyword IntrusionSet: