Taxonomy
In OpenCTI, taxonomies serve as structured classification systems that aid in organizing and categorizing intelligence data. This reference guide provides an exhaustive description of the platform's customizable fields within the taxonomies' framework. Users can modify, add, or delete values within the available vocabularies to tailor the classification system to their specific requirements.
For broader documentation on the taxonomies section, please consult the appropriate page.
Vocabularies
Default values are based on those defined in the STIX standard but can be tailored to better suit the organization's needs.
| Name | Used in | Default value |
|---|---|---|
| Account type vocabulary (account-type-ov) | User account | facebook, ldap, nis, openid, radius, skype, tacacs, twitter, unix, windows-domain, windows-local |
| Attack motivation vocabulary (attack-motivation-ov) | Threat actor group | accidental, coercion, dominance, ideology, notoriety, organizational-gain, personal-gain, personal-satisfaction, revenge, unpredictable |
| Attack resource level vocabulary (attack-resource-level-ov) | Threat actor group | club, contest, government, individual, organization, team |
| Case priority vocabulary (case_priority_ov) | Incident response | P1, P2, P3, P4 |
| Case severity vocabulary (case_severity_ov) | Incident response | critical, high, medium, low |
| Channel type vocabulary (channel_type_ov) | Channel | Facebook, Twitter |
| Collection layers vocabulary (collection_layers_ov) | Data source | cloud-control-plane, container, host, network, OSINT |
| Event type vocabulary (event_type_ov) | Event | conference, financial, holiday, international-summit, local-election, national-election, sport-competition |
| Eye color vocabulary (eye_color_ov) | Threat actor individual | black, blue, brown, green, hazel, other |
| Gender vocabulary (gender_ov) | Threat actor individual | female, male, nonbinary, other |
| Grouping context vocabulary (grouping_context_ov) | Grouping | malware-analysis, suspicious-activity, unspecified |
| Hair color vocabulary vocabulary (hair_color_ov) | Threat actor individual | bald, black, blond, blue, brown, gray, green, other, red |
| Implementation language vocabulary (implementation_language_ov) | Malware | applescript, bash, c, c++, c#, go, java, javascript, lua, objective-c, perl, php, powershell, python, ruby, scala, swift, typescript, visual-basic, x86-32, x86-64 |
| Incident response type vocabulary (incident_response_type_ov) | Incident response | data-leak, ransomware |
| Incident severity vocabulary (incident_severity_ov) | Incident | critical, high, medium, low |
| Incident type vocabulary (incident_type_ov) | Incident | alert, compromise, cybercrime, data-leak, information-system-disruption, phishing, reputation-damage, typosquatting |
| Indicator type vocabulary (indicator_type_ov) | Indicator | anomalous-activity, anonymization, attribution, benign, compromised, malicious-activity, unknown |
| Infrastructure type vocabulary (infrastructure_type_ov) | Infrastructure | amplification, anonymization, botnet, command-and-control, control-system, exfiltration, firewall, hosting-malware, hosting-target-lists, phishing, reconnaissance, routers-switches, staging, unknown, workstation |
| Integrity level vocabulary (integrity_level_ov) | Process | high, medium, low, system |
| Malware capabilities vocabulary (malware_capabilities_ov) | Malware | accesses-remote-machines, anti-debugging, anti-disassembly, anti-emulation, anti-memory-forensics, anti-sandbox, anti-vm, captures-input-peripherals, captures-output-peripherals, captures-system-state-data, cleans-traces-of-infection, commits-fraud, communicates-with-c2, compromises-data-availability, compromises-data-integrity, compromises-system-availability, controls-local-machine, degrades-security-software, degrades-system-updates, determines-c2-server, emails-spam, escalates-privileges, evades-av, exfiltrates-data, fingerprints-host, hides-artifacts, hides-executing-code, infects-files, infects-remote-machines, installs-other-components, persists-after-system-reboot, prevents-artifact-access, prevents-artifact-deletion, probes-network-environment, self-modifies, steals-authentication-credentials, violates-system-operational-integrity |
| Malware result vocabulary (malware_result_ov) | Malware analysis | benign, malicious, suspicious, unknown |
| Malware type vocabulary (malware_type_ov) | Malware | adware, backdoor, bootkit, bot, ddos, downloader, dropper, exploit-kit, keylogger, ransomware, remote-access-trojan, resource-exploitation, rogue-security-software, rootkit, screen-capture, spyware, trojan, unknown, virus, webshell, wiper, worm |
| Marital status vocabulary (marital_status_ov) | Threat actor individual | annulled, divorced, domestic_partner, legally_separated, married, never_married, polygamous, separated, single, widowed |
| Note types vocabulary (note_types_ov) | Note | analysis, assessment, external, feedback, internal |
| Opinion vocabulary (opinion_ov) | Opinion | agree, disagree, neutral, strongly-agree, strongly-disagree |
| Pattern type vocabulary (pattern_type_ov) | Indicator | eql, pcre, shodan, sigma, snort, spl, stix, suricata, tanium-signal, yara |
| Permissions vocabulary (permissions_ov) | Attack pattern | Administrator, root, User |
| Platforms vocabulary (platforms_ov) | Data source | android, Azure AD, Containers, Control Server, Data Historian, Engineering Workstation, Field Controller/RTU/PLC/IED, Google Workspace, Human-Machine Interface, IaaS, Input/Output Server, iOS, linux, macos, Office 365, PRE, SaaS, Safety Instrumented System/Protection Relay, windows |
| Processor architecture vocabulary (processor_architecture_ov) | Malware | alpha, arm, ia-64, mips, powerpc, sparc, x86, x86-64 |
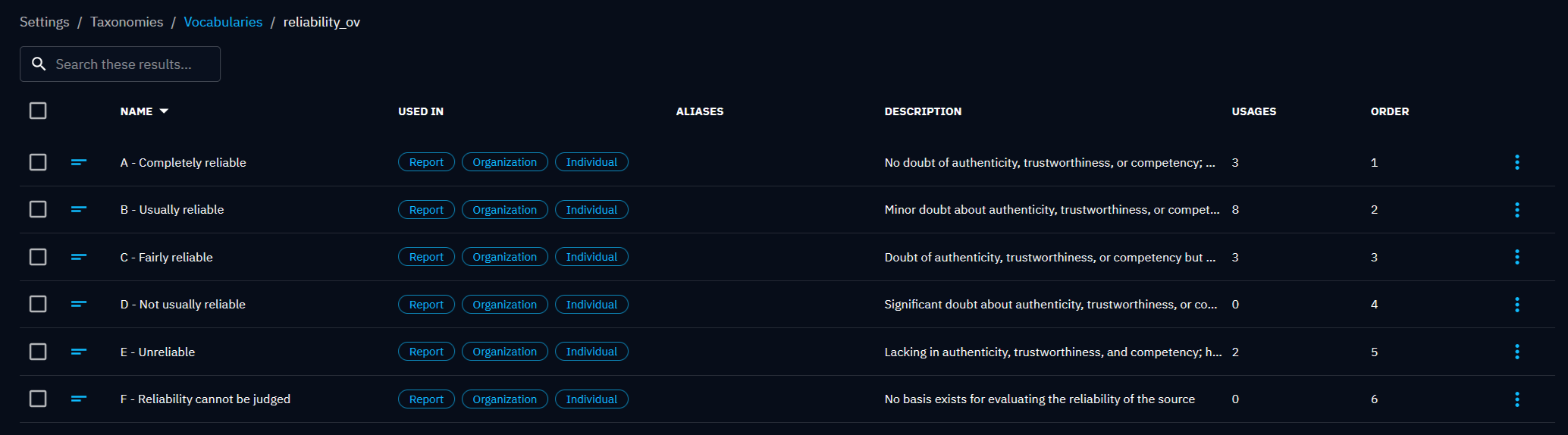
| Reliability vocabulary (reliability_ov) | Report, Organization | A - Completely reliable, B - Usually reliable, C - Fairly reliable, D - Not usually reliable, E - Unreliable, F - Reliability cannot be judged |
| Report types vocabulary (report_types_ov) | Report | internal-report, threat-report |
| Request for information types vocabulary (request_for_information_types_ov) | Request for information | none |
| Request for takedown types vocabulary (request_for_takedown_types_ov) | Request for takedown | brand-abuse, phishing |
| Service status vocabulary (service_status_ov) | Process | SERVICE_CONTINUE_PENDING, SERVICE_PAUSE_PENDING, SERVICE_PAUSED, SERVICE_RUNNING, SERVICE_START_PENDING, SERVICE_STOP_PENDING, SERVICE_STOPPED |
| Service type vocabulary (service_type_ov) | Process | SERVICE_FILE_SYSTEM_DRIVER, SERVICE_KERNEL_DRIVER, SERVICE_WIN32_OWN_PROCESS, SERVICE_WIN32_SHARE_PROCESS |
| Start type vocabulary (start_type_ov) | Process | SERVICE_AUTO_START, SERVICE_BOOT_START, SERVICE_DEMAND_START, SERVICE_DISABLED, SERVICE_SYSTEM_ALERT |
| Threat actor group role vocabulary (threat_actor_group_role_ov) | Threat actor group | agent, director, independent, infrastructure-architect, infrastructure-operator, malware-author, sponsor |
| Threat actor group sophistication vocabulary (threat_actor_group_sophistication_ov) | Threat actor group | advanced, expert, innovator, intermediate, minimal, none, strategic |
| Threat actor group type vocabulary (threat_actor_group_type_ov) | Threat actor group | activist, competitor, crime-syndicate, criminal, hacker, insider-accidental, insider-disgruntled, nation-state, sensationalist, spy, terrorist, unknown |
| Threat actor individual role vocabulary (threat_actor_individual_role_ov) | Threat actor individual | agent, director, independent, infrastructure-architect, infrastructure-operator, malware-author, sponsor |
| Threat actor individual sophistication vocabulary (threat_actor_individual_sophistication_ov) | Threat actor individual | advanced, expert, innovator, intermediate, minimal, none, strategic |
| Threat actor individual type vocabulary (threat_actor_individual_type_ov) | Threat actor individual | activist, competitor, crime-syndicate, criminal, hacker, insider-accidental, insider-disgruntled, nation-state, sensationalist, spy, terrorist, unknown |
| Tool types vocabulary (tool_types_ov) | Tool | credential-exploitation, denial-of-service, exploitation, information-gathering, network-capture, remote-access, unknown, vulnerability-scanning |
Customization
Users can customize the taxonomies by modifying the available values or adding new ones. These modifications enable users to adapt the classification system to their specific intelligence requirements. Additionally, within each vocabulary list, users have the flexibility to customize the order of the dropdown menu associated with the taxonomy. This feature allows users to prioritize certain values or arrange them in a manner that aligns with their specific classification needs. Additionally, users can track the usage count for each vocabulary, providing insights into the frequency of usage and helping to identify the most relevant and impactful classifications. These customization options empower users to tailor the taxonomy system to their unique intelligence requirements, enhancing the efficiency and effectiveness of intelligence analysis within the OpenCTI platform.